How Does a Hash Help Secure Blockchain Technology? Detailed Guide
In the complex landscape of public ledger advancements, hashing serves as a crucial foundation, providing security, integrity, and dependability to decentralized networks.
This mathematical process not only connects blocks in an unchangeable chain but also protects sensitive transaction information, converting intricate data into secure and easily manageable digital signatures.
Whether you’re curious about how Bitcoin transactions remain untampered or how decentralized systems resist malicious actors, realizing the role of hashing is key to appreciating the innovative design of blockchain tools.
This article explores the technical details of hashing and answers the key question: “How does a hash help secure blockchain technology?”
Key Takeaways
- Hash operations generate unique outputs, instantly detecting tampering and preserving blockchain immutability.
- Cryptographic hashes allow nodes to validate blocks independently, ensuring trust without shared authority.
- From linking blocks to powering Proof-of-Work and verifying transactions, hashing is vital to blockchain stability and reliability.
What Does Hash Stand For?
A hash is the result of a process called hashing, in which an input—such as a string of text, a file, or any form of digital data—is transformed into a fixed-length string of characters, typically in hexadecimal or binary format.
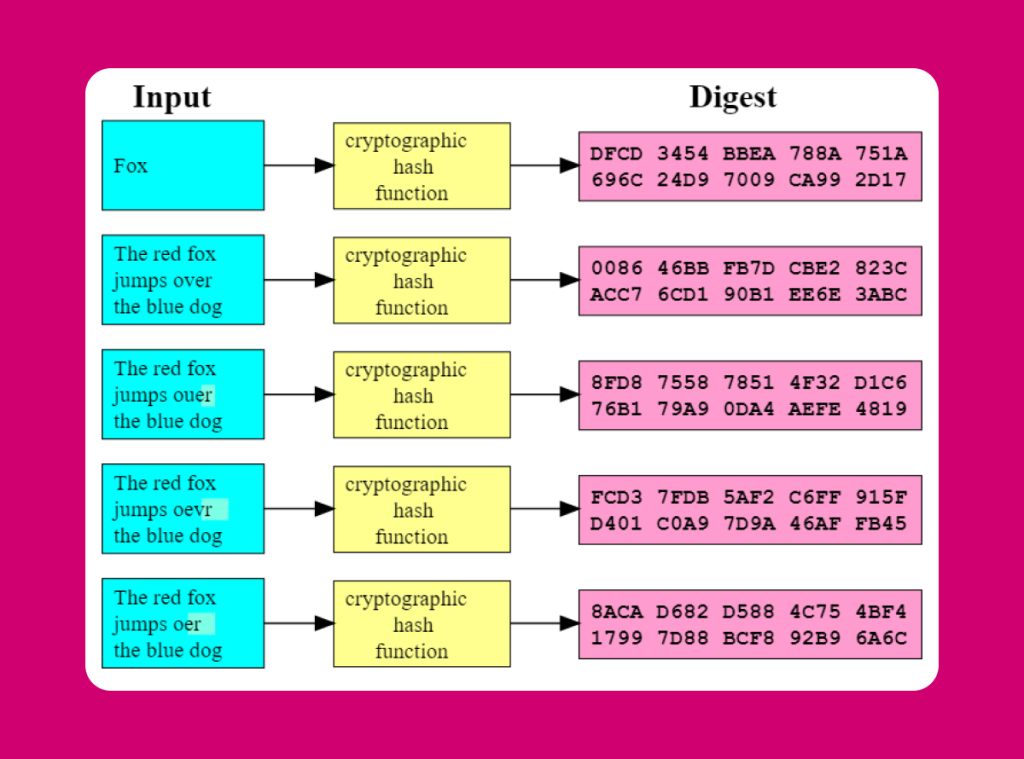
This transformation is achieved through a crypto program identified as a hash function. Hashing is a basic component of modern cryptography and is vital in several contexts, considering data preservation, digital endorsements, and blockchain advancements.
Fast Fact
A single hash from SHA-256, the algorithm used in Bitcoin, can represent more data combinations than there are atoms in the observable universe, highlighting its unmatched capacity for secure and unique data representation.
Hash Functions Used in Blockchain
Hash functions are essential components of blockchain technology, providing the foundation for data integrity, security, and immutability. Blockchain networks rely on these cryptographic algorithms to process orders, link blocks, and ensure tamper resistance.
Here’s a detailed explanation of the hash functions commonly used in blockchain:
SHA-256 (Secure Hash Algorithm 256-bit)
SHA-256 is blockchain technology’s most widely used cryptographic hash utility, particularly in Bitcoin. Developed by the NSA and part of the SHA-2 family, it generates a fixed 256-bit (64-character) hash for any input.
In blockchain, SHA-256 powers the PoW consensus algorithm by requiring miners to solve complex puzzles. It also ensures block immutability by linking each block with the SHA-256 hash of the previous block. Known for its security, collision resistance, and computational efficiency, SHA-256 is ideal for blockchain applications.
RIPEMD-160
RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest) is a 160-bit hash function widely used in blockchain for compact and secure hashing.
Bitcoin creates wallet addresses using RIPEMD-160 alongside SHA-256, assuring confidentiality while maintaining a manageable address size. Its lightweight nature and collision resistance make RIPEMD-160 suitable for specific cryptographic needs in blockchain architectures.
Keccak (SHA-3)
Keccak, the winning algorithm of the NIST SHA-3 competition, is a sponge-based cryptographic hash calculation. While distinct from SHA-2, it is often referred to as SHA-3.
Ethereum extensively uses Keccak-256 for transaction verification, block mining, and address creation. Its sponge construction makes it resistant to cryptanalytic attacks, offering enhanced security. Keccak is valued for its flexibility and high resistance to preimage attacks, ensuring robust blockchain applications.
Blake2
Blake2 is a high-speed cryptographic hash code optimized for both software and hardware. As a successor to the Blake algorithm (an SHA-3 competition finalist), Blake2 is faster than SHA-2 while maintaining strong cryptographic properties.
Some altcoins use it for its efficiency and performance benefits. Blake2’s efficiency, security, and customizability suit emerging blockchain technologies.
Ethash
Ethash is a memory-intensive hash function explicitly developed for Ethereum’s Proof-of-Work algorithm. It ensures decentralization by being GPU-friendly and resistant to ASIC mining.
Ethash underpins Ethereum’s mining process, promoting secure and distributed consensus. Its memory-hard design makes it resistant to specialized mining hardware, supporting Ethereum’s goal of decentralized participation.
Scrypt
Scrypt is a password-based key derivation function designed to be mathematically and resource-constrained. It is widely adopted in blockchain systems to resist ASIC mining.
Litecoin uses Scrypt for its PoW algorithm, making mining accessible to individual users with general-purpose hardware. Many altcoins also utilize Scrypt due to its balance of security and efficiency. Its memory-hardness ensures resistance to custom hardware attacks, promoting decentralization in blockchain networks.
Key Properties of Blockchain Hash Functions
Hash functions are integral in distributed ledger technology, providing decentralized systems’ stability, unity, and reliability. Below are the detailed key properties that make hash computation indispensable in blockchain use cases:
Deterministic Output
A hash function always produces the same output for the same input. In the ledger system, this attribute assures that any given record block will always result in a consistent hash value.
This deterministic nature is crucial for verifying transactions and retaining the integrity accuracy of the distributed ledger, as even a slight change in input data (e.g., a single bit) will result in a completely different hash.
Fixed-Length Output
Hash functions generate a fixed-length output regardless of the size of the input data. For instance, SHA-256 always produces a 256-bit hash. This uniformity makes hash functions efficient for storing and comparing data in the blockchain, enabling fast and compact validation of blocks and transactions.
Preimage Resistance
Preimage resistance means deducing the starting input from its hash output is technically futile. In blockchain, this property ensures that the original transaction details cannot be reverse-engineered from the hash, providing confidentiality and security for sensitive data.
Collision Resistance
Collision resistance ensures that it is nearly impossible for two different inputs to yield the same hash response. This is critical in blockchain, as hash collisions would undermine the uniqueness of blocks, leading to potential inconsistencies or vulnerabilities in the system. By preventing collisions, the blockchain maintains its validity and trustworthiness.
Avalanche Effect
The avalanche effect refers to the property where a slight change in input data results in a significantly different hash output. For example, altering even a single character in a transaction will produce an entirely new hash. This precision assures that any tampering with blockchain data is immediately detectable, enhancing the system’s immutability.
Fast Computation
Hash functions are designed to compute outputs quickly, enabling efficient processing of transactions and blocks. This speed is essential for maintaining the performance and scalability of blockchain systems, especially in high-throughput environments like Bitcoin and Ethereum.
Unidirectional Processing
Hash functions are one-way algorithms, meaning that while it is easy to compute a hash from input records, it is mathematically infeasible to reverse the process. This one-way nature is critical for maintaining the security of digital signatures, transaction details, and block validation in blockchain technology.
Efficient Verification
Blockchain relies on the ability to verify data credibility quickly. Hash functions assure timely verification by allowing nodes to compare hash values without reprocessing the entire dataset. For instance, verifying a block’s validity only requires comparing its hash with the expected value.
Independence from Input Size
Hash functions can handle inputs of arbitrary length, from a few bytes to gigabytes of data, and still produce a fixed-length output. This versatility allows blockchain systems to process and secure various transactions and blocks uniformly.
Resistance to Cryptanalysis
Modern cryptographic hash functions are designed to resist known forms of cryptanalysis, such as differential and linear attacks. This resilience is crucial for long-term blockchain validity, ensuring the system remains robust against evolving threats.
How Does a Hash Help Secure Blockchain Technology?
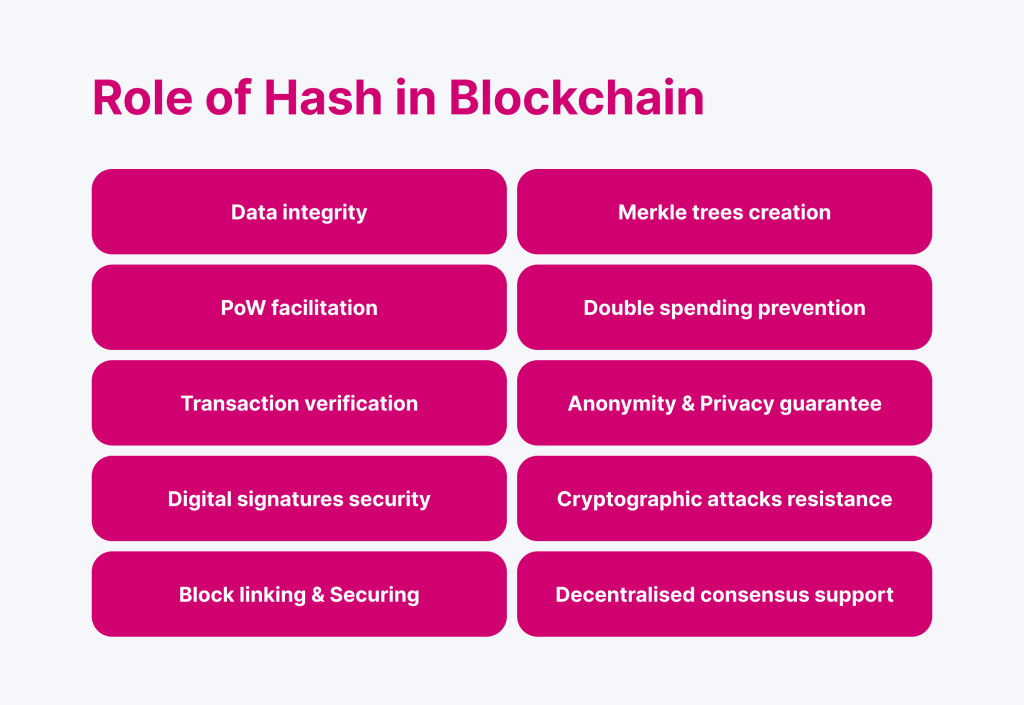
Hashing is central to blockchain technology, assuring its robustness, wholeness, and decentralized functionality. Here are the key ways hashing achieves these objectives:
Ensuring Data Integrity
Hashing creates a unique fixed-length output (hash) for any input data. In a blockchain, each block contains the previous block’s data hash. This chaining mechanism ensures that even a minor alteration in one block produces a completely different hash, breaking the chain and making tampering immediately evident.
This property safeguards the solidity of the blockchain by making data immutable and secure from unauthorized modifications.
Facilitating Proof-of-Work (PoW)
In PoW-based blockchains like Bitcoin, hashing is central to the mining process. Miners approach intricate programming puzzles by finding a hash that meets specific criteria (e.g., starting with a certain number of zeros). This ensures that adding new blocks requires significant computational effort, deters malicious actors, and maintains the network’s security and decentralization.
Enhancing Transaction Verification
Every transaction in a blockchain is hashed to create a unique digital fingerprint. This hash verifies that the transaction data has not been altered. Nodes in the network can quickly validate transactions by comparing their hashes, ensuring the fast and secure processing of blockchain operations.
Securing Digital Signatures
Hashing is integral to the generation and verification of digital signatures. When users sign a transaction, they hash the transaction data and encrypt it with their private key. The resulting digital signature can be verified by others using the sender’s public key and the hash, ensuring the transaction’s authenticity and non-repudiation.
Linking and Securing Blocks
Each block in a blockchain contains the preceding block’s encrypted key, producing an incorruptible chain of blocks. This linkage ensures that altering one block would require recalculating the hashes of all subsequent blocks, an infeasible task due to the computational energy required. This feature is key to blockchain’s tamper-resistance and security.
Enabling Merkle Trees
Merkle trees are data structures used in blockchain to efficiently summarise and verify large sets of transactions. By hashing transactions into a hierarchical structure, Merkle trees allow nodes to verify individual transactions without downloading the entire blockchain. This enhances scalability, reduces storage requirements, and ensures secure transaction verification.
Preventing Double Spending
Hashing guarantees that each operation on the blockchain is unique and irreversible. By creating a cryptographic link between transactions, hashing prevents users from spending the same cryptocurrency multiple times, preserving the trust and reliability of the blockchain system.
Providing Anonymity and Privacy
While blockchain data is transparent, hashing promotes user privacy by obscuring sensitive information. Wallet addresses and transaction details are hashed, creating pseudonymous identifiers that secure user identities without compromising the transparency of the network.
Resisting Cryptographic Attacks
Modern cryptographic hash algorithms, such as SHA-256 and Keccak, are designed to resist preimage attacks, collision attacks, and other forms of cryptanalysis. This resilience assures that the ledger systems remain secure against evolving computational and cryptographic threats.
Supporting Decentralized Consensus
Hashing ensures all nodes in a blockchain network can independently confirm blocks and swaps. By comparing hash values, nodes achieve consensus without needing a local authority, maintaining the decentralized nature of distributed ledger protocols.
Conclusion
Hashing is an absolute blockchain encryption component, transcending its role as merely a mathematical operation. It converts data into distinct, fixed-length outputs, enhancing data permanence, streamlining transaction verification, and safeguarding user privacy. Cryptographic hash operators such as SHA-256 and Keccak have strengthened blockchain infrastructures, providing robust defenses against tampering, fraud, and various cyber threats.
As blockchain technology evolves, hashing will remain a mainstay, driving innovation and trust in decentralized networks. Thus, perceptive how hashing secures blockchain technology deepens your appreciation of its robustness and highlights the future implications of secure, decentralized ecosystems.
FAQ:
What is a good hash rate in blockchain mining?
A higher hash rate, measured in terahashes or petahashes per second, improves mining performance and the likelihood of earning rewards in algorithms like Bitcoin.
How dependable is public ledger technology with hashing?
Hashing boosts data longevity, prevents tampering, and supports decentralized consensus, making the ledger highly secure.
What’s the difference between tokenization and hashing?
Tokenization replaces data with retrievable tokens, while hashing transforms data into irreversible cryptographic outputs.
How does hashing prevent double spending?
Hashing assures transaction uniqueness and links them cryptographically, preventing duplicates and eliminating double-spending.