What Is a Crypto Dusting Attack? Why You Should Be Concerned
With the development of cryptocurrencies, users encounter new and new security threats. One such threat is the crypto dusting attack – where tiny amounts of crypto are sent to multiple wallet addresses. While this may seem insignificant, it can have serious consequences for users’ privacy and security.
In this article, we will delve into the world of crypto dusting attacks, their potential risks, and what users can do to safeguard their assets.
Key Takeaways:
- In crypto, dust refers to tiny amounts of digital currency left after executing transactions.
- Crypto dusting attacks are intended to compromise user privacy.
- These attacks are usually performed by hackers and other malicious actors. However, sometimes network testers and advertisers also send dust transactions.
What Is Dust?
The term “dust” refers to the tiny and nearly insignificant amounts of a particular cryptocurrency unit. It is often considered to be the leftover or residual amounts after executing trading orders within a crypto exchange or when transferring from one wallet to another.
Usually, the dust of a certain coin is either the same amount or less than the transaction fee that is associated with it. For instance, in the case of Bitcoin, dust can be as low as 546 satoshis (0.00000546 BTC), which is the smallest denomination of BTC.
How is dust calculated? The dust limit is determined based on the size of inputs and outputs for a transaction. For regular Bitcoin transactions (non-SegWit), the calculation results in a dust limit of 546 satoshis. However, for native SegWit transactions, the limit is slightly lower at 294 satoshis.
Crypto dust accumulates over time, and while there may be no way to trade it, some exchanges offer users the option to convert these small amounts into their native tokens or use them for future trades. In certain cases, dusting can even be used as a unique advertising method, where promotional messages are included in the dust transactions as an alternative to email campaigns.
What is a Crypto Dusting Attack?
Sadly, the dust can be exploited in malicious ways. Dusting attacks have become a growing concern within the cryptocurrency community. A crypto dusting attack occurs when cyber criminals send small amounts of crypto to multiple addresses all over the blockchain.
The goal of these attacks is not to steal cryptocurrency directly but rather to compromise the privacy of wallet owners through tracking their funds. By performing a combined analysis of these addresses, attackers can attempt to link them to personal data and potentially identify the individuals or organizations behind the wallets.
The implications of a successful dusting attack can be severe. Attackers may use obtained data for phishing attempts, cyber-extortion threats, blackmail, or even identity theft.
While dusting attacks were initially observed in the Bitcoin network, they can also occur in other blockchains, such as Ethereum and BNB. Dusting attacks rely on blockchains that operate on a traceable and public ledger, where the transaction history is visible to anyone.
How Crypto Dust Attacks Are Executed
Dusting attacks begin with the attacker sending tiny amounts of crypto to various addresses, which are typically chosen at random.
Once the dust has been sent, the attackers can use blockchain information to track the movements of these funds and identify which wallets they have been consolidated into. This is possible due to the traceability and transparency of blockchain technology. Dust attack is more effective when the victim mixes the dust with their wallet’s balance and then uses those funds to carry out different transactions.
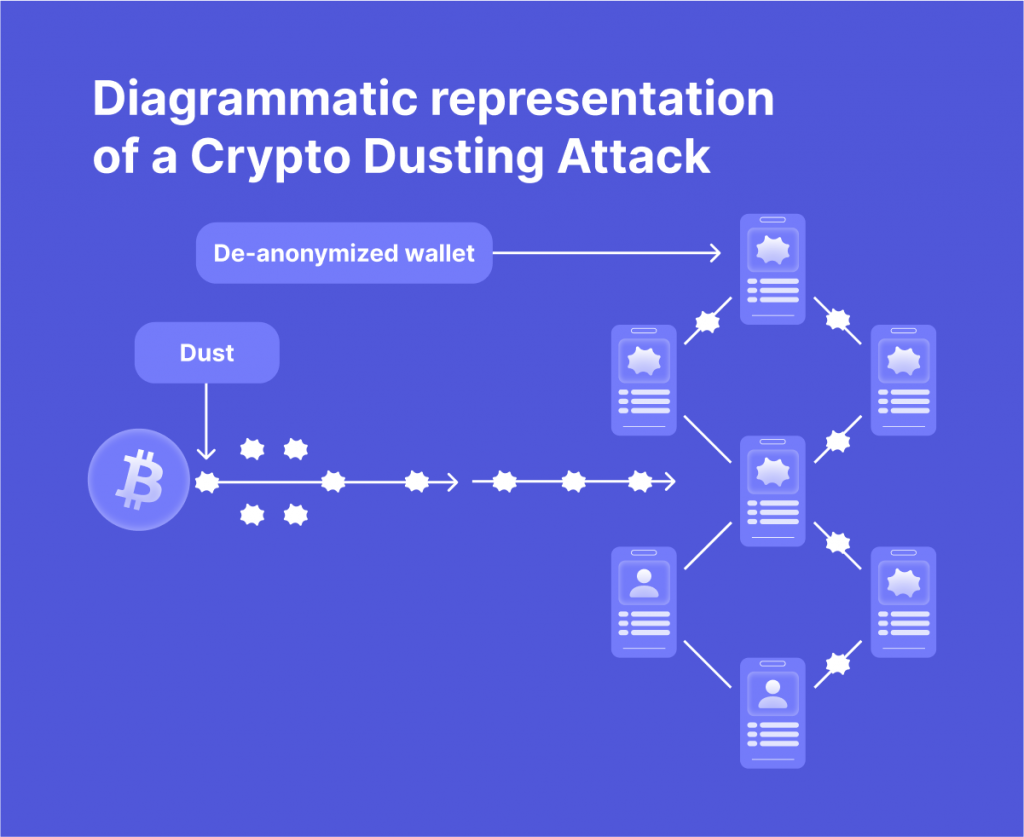
The danger lies in when these dust-laden transactions are sent to off-blockchain centralized organizations, such as exchanges or wallet providers. These entities are required by law to comply with KYC regulations, which means they must collect and store the personal data of their users.
By tracing the dust back to these centralized platforms, attackers can potentially identify the victim’s personal information. This puts them at risk of phishing attacks, blackmail, or other sensitive data theft scams.
The most susceptible crypto addresses are those that use the UTXO system, such as Bitcoin. With UTXO, each transaction generates a new address for any remaining funds (similar to receiving change from a merchant).
Different Purposes of Dusting Attacks
It’s crucial to note that while dusting attacks can have nefarious intentions, not all of these attacks are crypto scams. There are a number of different parties who may be motivated to execute such an attack.
Criminal Organizations
One category that has been known to carry out dusting attacks is criminal groups. These groups may have a variety of motivations, including attempting to de-anonymize individuals with large cryptocurrency holdings. If an attack is successful, attackers can potentially track where the funds are being sent and target those with high balances for further attacks such as phishing scams or cyber-extortion.
However, criminals may also use dusting attacks as a means of obfuscation. In the event that they receive a tip that law enforcement is closing in on them, they may use dusting to spread their dirty money across multiple wallets, making it harder for authorities to track.
State Authorities
Believe it or not, government agencies may also be behind dusting attacks. Different government entities have been known to use dusting as a means of connecting users or groups to specific cryptocurrency addresses. This can be particularly useful in cases involving gangs dealing in contraband, large criminal networks, money laundering operations, or tax evasion.
Blockchain Analytics
Some entities may also use dusting attacks for research purposes or to gather evidence for criminal investigations. In some cases, they may even work with blockchain analytics firms to analyze the results of a dusting attack.
Spammers
Dusting attacks may also be used as a form of advertising. Advertisers can include messages in the dust transaction that reach a large number of crypto users. This is similar to an email blast but with the added benefit of being directly integrated into the blockchain.
Network Stress Testers
Finally, some individuals or groups may use dusting attacks as a way to test the throughput or bandwidth of a network. By sending large amounts of dust in a short period of time, they can see how the network handles the increased transaction volume. This can help identify potential vulnerabilities and improve the overall functionality of the network. However, some may also use this tactic as a form of network spam, clogging and slowing down the network for malicious purposes.
Can Dusting Attacks Steal Your Cryptocurrency?
A traditional dusting attack can’t directly drain your crypto assets. The main objective of a dusting attack is to deanonymize wallet owners and compromise their privacy. However, in the last couple of years, dusting attacks have evolved into more advanced tactics that can result in the actual theft of cryptocurrency.
One of these tactics involves luring users into fake airdrop scams. Airdrops are giveaways of free tokens, often used as a marketing strategy for new projects. Phishing sites that closely resemble authentic platforms are used to promote these scams. By connecting their wallets to these sites, victims unknowingly give hackers control of their tokens and NFT assets, resulting in the theft of their cryptocurrency.
It’s important for users to exercise caution when participating in airdrops or interacting with DApps and Web3 services. Wallets that can be accessed through a browser, such as MetaMask and Trust Wallet, are highly susceptible to dusting attacks due to their common use for these purposes.
Well-Known Examples of Dusting Attacks
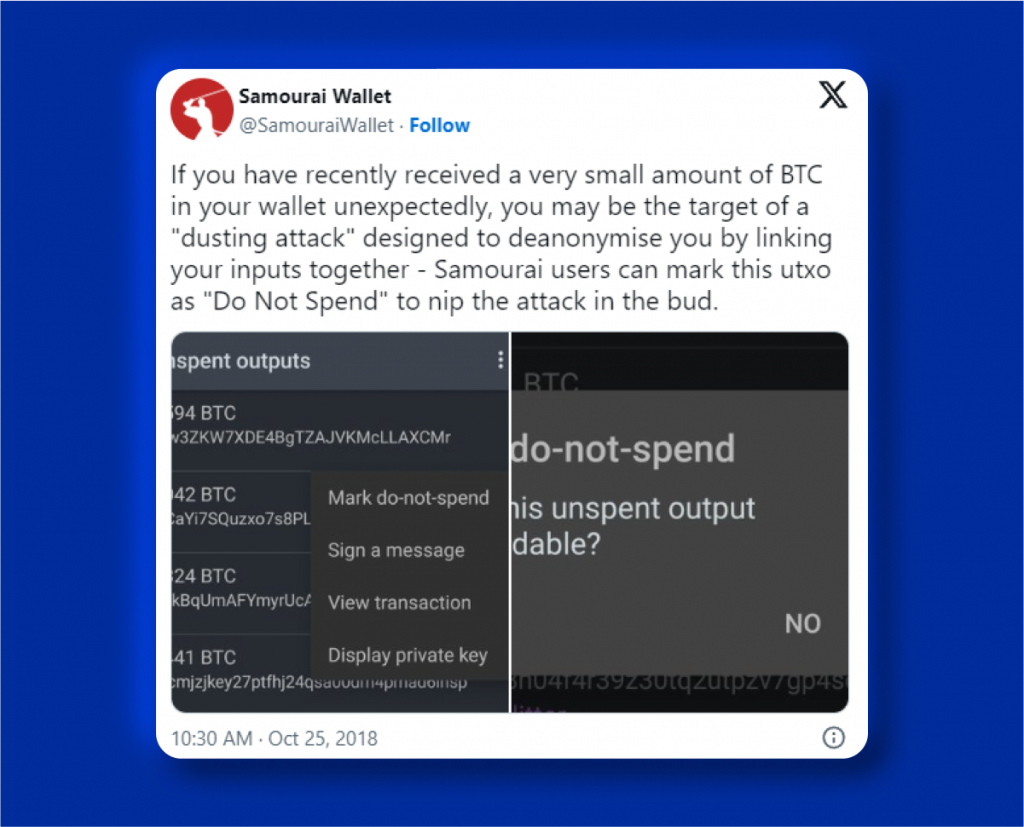
One well-known example of a dusting attack occurred in October 2018 when users of Samourai Wallet were targeted. The company quickly took action by warning its users about the attacks and implementing measures such as real-time alerts for dust tracking and a “Do Not Spend” feature.
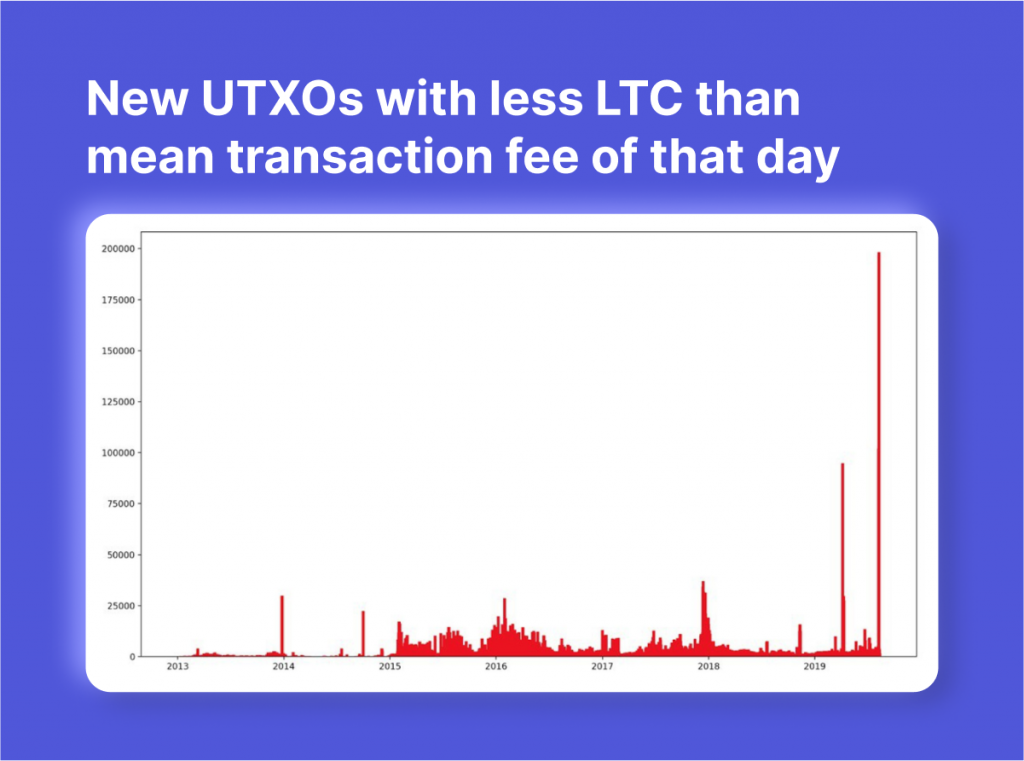
Another notable incident happened in August 2019 when Litecoin was subjected to a similar attack. This time, approximately 200,000 wallets were affected, with only 50 of them initially being identified by cryptocurrency exchange Binance.
Furthermore, some companies have even used dusting attacks as a marketing tool. In one instance, Steemit sent out news about their platform’s innovations along with a small amount of STEEM tokens as a reward for users. Similarly, BestMixer.io sent out ad spam along with a small amount of BTC as part of their marketing strategy.
How to Avoid Dusting Attacks?
To avoid becoming a victim of such an attack, here are some precautions you can take:
1. Stay Alert
The first step in protecting yourself from dusting attacks is being aware of their existence. Keep an eye on your wallet’s transaction history and be cautious if you suddenly receive small sums of crypto that cannot be spent or withdrawn.
2. Convert Dust into Native Tokens
You can opt for platforms that automatically convert crypto dust into native tokens. This not only protects your wallet from potential attacks but also allows you to use it for future transactions.
3. Utilize Hierarchical Deterministic (HD) Wallets
Consider using Hierarchical Deterministic (HD) wallets that automatically generate a new address for each transaction. This makes it extremely challenging for attackers to connect the dots and ensures the safety of your funds.
4. Use Privacy Tools
Privacy tools such as the TOR browser or VPN can greatly increase anonymity when making cryptocurrency transactions. By masking your IP address, these tools make it harder for hackers to track your activities and link them to your wallets.
5. Be Mindful of Other Crypto Scams
While dusting attacks may be a concerning threat in the cryptocurrency world, it’s also important to be mindful of other cyber threats in crypto. Keep your devices and software up-to-date, use strong passwords and 2FA, store your crypto in cold wallets, and be cautious when clicking on suspicious links. These can help prevent falling victim to cybercrime.
Closing Thoughts
While dusting attacks are a concern, it is important to remember that they primarily target individuals or organizations with large cryptocurrency holdings or those in high-risk areas. For the average cryptocurrency user, dusting attacks are more of an annoyance than a significant threat. If you take precautions and remain vigilant, these attacks can be minimized, and you can protect your privacy and security.
FAQs
What is the most common crypto wallet hack?
The most common crypto wallet hack is phishing. This type of attack involves malicious actors sending emails that deceive crypto owners into divulging sensitive information or downloading malware, which can then be used to access their crypto wallet and steal their coins. Phishing attacks are one of the top digital threats facing cryptocurrency users today.
Why do hackers prefer cryptocurrency?
Hackers prefer cryptocurrency for its anonymity and decentralization. Cryptocurrencies are not controlled by any central authority, making it harder for law enforcement agencies to track transactions and identify the individuals behind them. This makes cryptocurrencies an ideal choice for cybercriminals who want to remain undetected while carrying out illegal activities such as money laundering, ransomware attacks, and drug trafficking.
Are all crypto wallets safe?
No, not all crypto wallets are safe. As with any digital platform, there is always a risk of cyber attacks. However, using a hardware wallet, also known as a cold storage wallet, can significantly reduce the risk of losing funds. These wallets store your private keys offline, making them less vulnerable to online threats and hacking attempts.
What precautions can I take to protect my crypto wallet?
There are several precautions you can take to protect your crypto wallet and prevent it from being hacked. Some of these include:
- Use a strong password and 2FA: It is important to use a strong and unique password for your crypto wallet. This means using a combination of upper and lower case letters, numbers, and special characters. Additionally, enabling 2FA adds an extra layer of security by requiring a code from your phone or email before accessing your wallet.
- Keep your private keys safe: Private keys are like the password to your crypto wallet. They allow you to access and spend your cryptocurrency, so it is important to keep them safe. Consider storing them offline or in a secure hardware wallet.
- Be cautious of phishing scams: Phishing scams involve tricking individuals into giving away their personal information, such as login credentials. Don’t click on any links in emails or messages that ask for your wallet information, and always double-check the URL.
- Regularly update your software and devices: Keep your devices and software up to date with the latest security patches to protect against potential vulnerabilities.
- Backup your wallet: Make regular backups of your wallet in case of any technical failures or if you lose access to your device.



